What is face recognition?
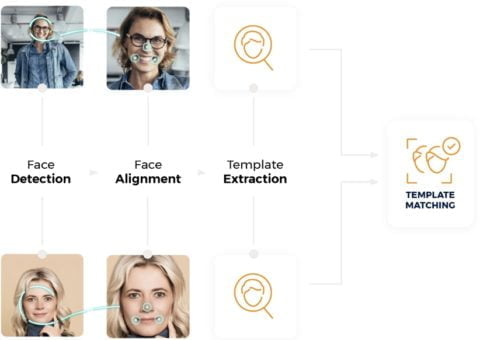
Facial recognition system is a sophisticated way to verify or ascertain someone’s identity using an algorithm that processes a digital image or video frame. It picks out distinguishing features of someone’s face shown in an image and matches these to the faces already logged within a database. It is growing in popularity, with new uses for it being developed all the time. Digital images and video stills are becoming clearer and easier to pick out distinct people and faces, while the matching software and algorithms are benefitting from increased data sources and accuracy.
The use of facial recognition and data is also increasingly becoming a vital part of commercial identification, helping to target individuals and personalize sales and marketing messages. Facial recognition is also increasingly used in automatic image indexing, human-technology interactions, and video surveillance systems. Technological advances are constantly happening, with significant upgrades.
What are the benefits of Facial Recognition?
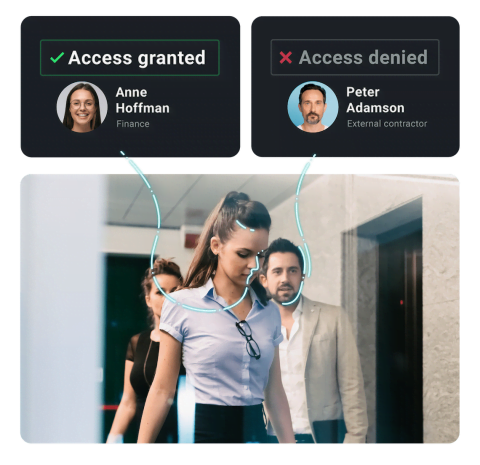
There are many benefits to facial recognition software. A key area is improved security, both in public areas and for companies and organizations, such as banks, schools, prisons, and airports. It can help law enforcers to identify people of interest more quickly and work out their movements to track them down and prevent them from causing any harm.
It can also speed up identity checks in airports, at borders, and for personal admin tasks, such as banking or entering and exiting workplaces and other buildings. It also works very well with social media, providing an alternative, non-invasive method of accessing accounts rather than inputting passwords or codes. Retailers and marketing professionals can also use the technology to tailor advertisements and commercial messages to customers more precisely.