Capturing Biometric Sample definition
Capturing a biometric sample is the process of acquiring raw data that represents a person’s biometric trait, such as a face, fingerprint, iris, or palm, using a capture device such as a camera or scanner. The output is a biometric sample that can be assessed for quality and then converted into a biometric template for later comparison. In practice, capturing a biometric sample may be as simple as a quick selfie on a phone during digital onboarding or as controlled as a guided capture at a border kiosk.
Why Capturing a Biometric Sample Matters?
Everything that happens downstream, including extraction, matching, and decision-making, depends on the quality of the captured sample. If the image is blurry, poorly lit, occluded (e.g., face behind a mask or hair), or otherwise defective, the system will either fail to extract a robust template or produce a template that raises false rejects/accepts later.
International standards describe how to measure and report this quality so organizations can set thresholds and get consistent results across devices and sites. The ISO/IEC 29794 series provides the general framework for biometric sample quality, and modality-specific parts define what good means for finger, face, and iris capture.
A good capture is fit for purpose: sharp enough, well-exposed, and properly framed to preserve the detail that matching algorithms need. For example, face captures should meet scene, photographic, and digital constraints defined for interoperability, while finger and iris captures must achieve specific resolution and focus properties to reveal fine ridge detail or iris texture. These requirements aren’t arbitrary as they correlate strongly with recognition performance and reduce operator re-takes and user frustration.
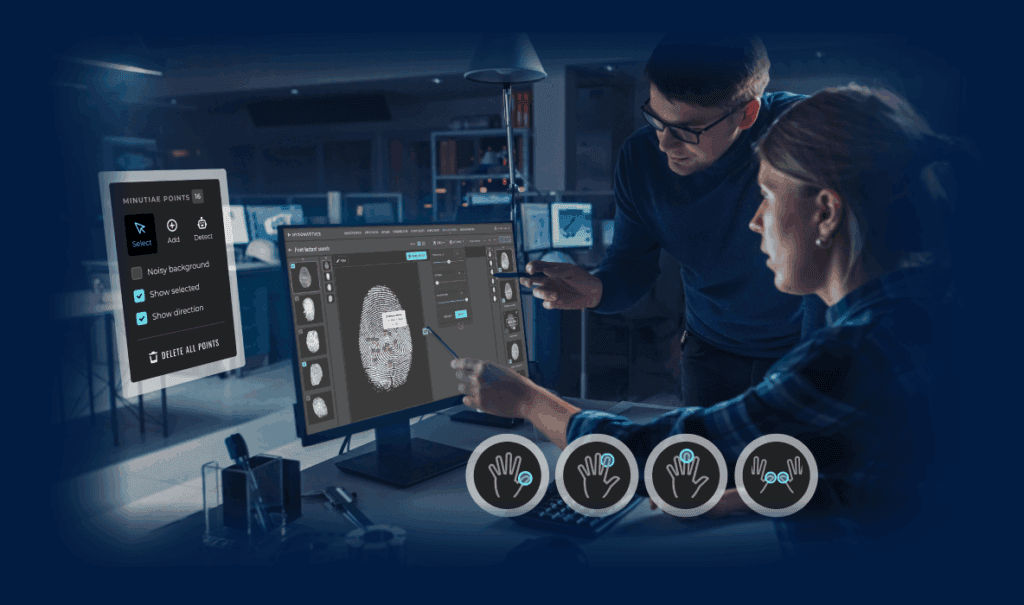

Mapping the Capture Pipeline
- Sensing: A capture device (camera, fingerprint scanner, or iris sensor) acquires raw data. For faces, this is usually a visible-light or near-infrared (NIR) camera. For fingerprints, they are optical/capacitive/ultrasonic sensors, and for irises, they’re typically NIR cameras to highlight iris patterns.
- Real-time feedback & usability: During capture, systems often provide live guidance: “Move closer,” “Look straight,” “Hold steady,” or “Place your finger again.” Well-designed capture interfaces reduce failure to acquire (FTA) by correcting lighting, pose, and framing in the moment. This emphasis is reinforced by usability research programs that tie ergonomic capture design to successful outcomes.
- Quality assessment: After the shutter click (or finger press), quality algorithms score the sample. For fingerprints, the widely used NFIQ 2 score predicts whether ridge detail is good enough for matching. For faces, assessments check sharpness, illumination, pose, occlusions, and other indicators; NIST’s face image quality work relates these factors to verification outcomes at scale.
- Decision & storage: If a sample meets the threshold, it proceeds to extraction (template creation) and enrollment or verification. If not, users get a re-capture prompt. Organizations can log anonymized quality stats to pinpoint problematic cameras, kiosks, or lighting setups and keep the whole pipeline healthy.
Modalities and How Capture Differs
Face Capture
Face capture is now part of daily life, anywhere from unlocking a phone or checking in at an airport to verifying your identity for an online service. Wherever it happens on a smartphone during onboarding, at a border kiosk, or in a building lobby, the goal is to capture a face image that is clear, evenly lit, and accurate enough to represent you in the system. To achieve this, factors like lighting, pose, facial expression, and motion control all matter. The camera needs to see both eyes open, a neutral expression, and no obstructions like hats, sunglasses, or shadows. Even something as small as a head tilt or uneven lighting can degrade the system’s ability to recognize the face correctly later.


Fingerprint Capture
Fingerprint capture remains one of the most widely used biometric methods, from border control and police booking to everyday time-and-attendance systems or smartphone unlock sensors. For a fingerprint to be usable, the scanner must capture clear ridge detail at a standard resolution, typically 500 pixels per inch for official ten-print devices. The finger’s placement, the evenness of pressure, and even the moisture of the skin affect the result. A too-dry or overly moist finger can blur the ridge lines, while movement during capture causes smudging or loss of fine detail.


Iris Capture
Iris capture sits at the high end of biometric assurance. It’s commonly used at eGates, in secure facilities, or in national ID programs where maximum accuracy is essential. The iris pattern—those fine rings of color and texture around the pupil—is unique to each person and remains stable for life. To capture it properly, specialized cameras use near-infrared (NIR) light to illuminate the eye safely and make the intricate pattern stand out. Distance, focus, and the steadiness of the subject are crucial: too close, too far, or even slight movement can blur the pattern and make matching unreliable.
When done right, iris recognition is exceptionally accurate, even at scale. However, it demands a cooperative subject and a steady stance, which are factors that become challenging in busy walk-through gates or mobile contexts. The best systems strike a balance by giving users just enough guidance to capture quickly without feeling intrusive, ensuring security doesn’t come at the cost of usability.


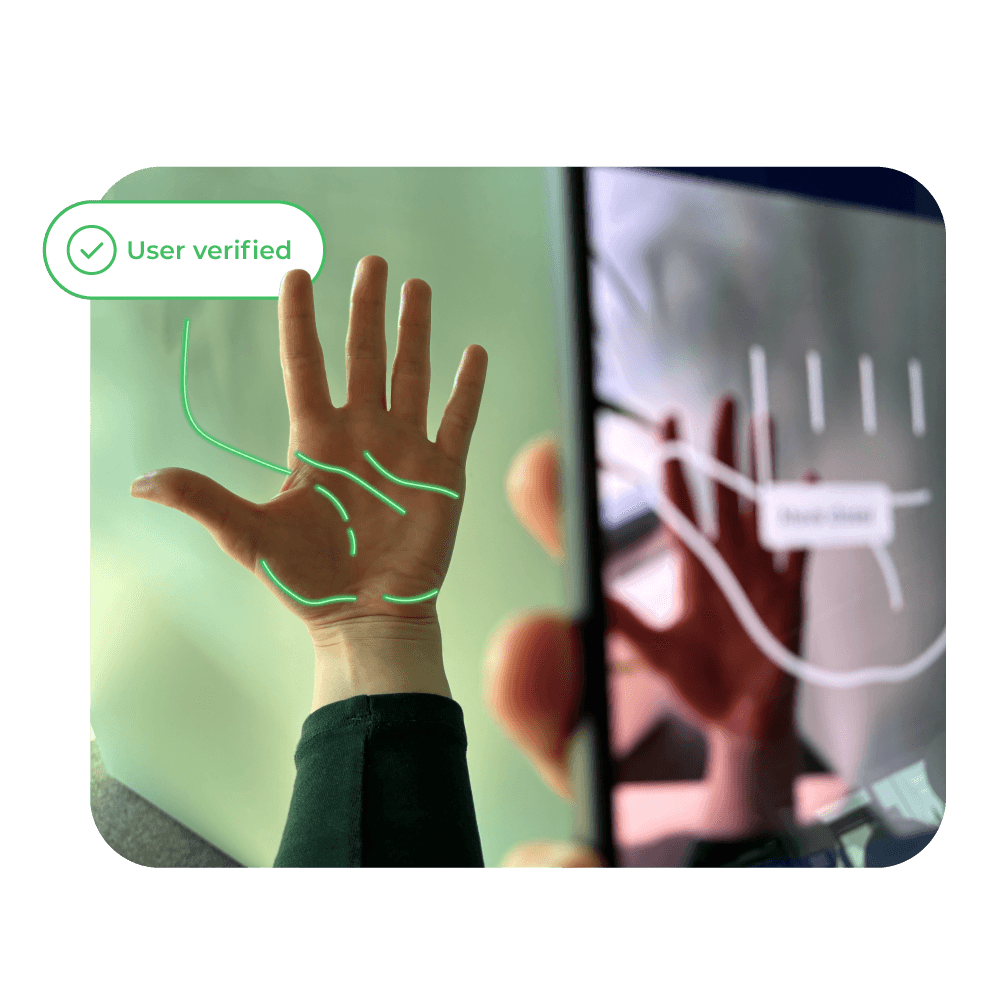
Palm Capture
Palm capture focuses on recognizing either the palmprint: the surface ridges of the hand or the palm vein pattern beneath the skin. In most modern systems, it’s a quick, contactless process where users simply hold their hand steady over a camera. The system ensures the palm is centered, well-lit, and still, capturing enough detail for accurate recognition.
The appeal of palm biometrics lies in its clean, touch-free use and strong security. Because the imaging area is larger than a single finger, it provides more unique features to analyze, improving accuracy. Vein-based capture adds an extra layer of protection since veins are invisible and internal, making them nearly impossible to fake. As a result, palm recognition is becoming increasingly popular in workplaces, hospitals, and public facilities that value both hygiene and quick, reliable access.

Enrollment capture vs. Verification capture
Verification and enrollment are two sides of the same coin but have very different goals. Enrollment is the moment of truth in simple terms. It’s the system’s first opportunity to record your biometric data. Because this data becomes your permanent reference, the process is strict and controlled. Operators or guided interfaces often take multiple shots, use bright, even lighting, and enforce high-quality thresholds. National ID programs and passport agencies typically follow ISO/IEC and ICAO rules to ensure that the images they enroll will last and perform well over years of use. The aim is to capture a perfect reference template that future verifications can depend on.
Verification, on the other hand, happens repeatedly and needs to be fast and convenient. It’s what you do every time you unlock a phone, enter a building, or pass through an airport gate. Since the user has already been enrolled, the system only needs to confirm that the live biometric matches the stored reference. The thresholds can be slightly more forgiving to account for daily variations like lighting or small changes in appearance, but quality still matters.
Liveness and Presentation Attack Detection (PAD) at Capture Time
Biometric capture isn’t only about clarity but also the first line of defense against deception. Attackers have tried everything from printed photos and silicone fingers to high-resolution videos to trick systems. That’s why liveness detection, formally known as Presentation Attack Detection (PAD), has become a standard part of modern capture workflows.
In everyday use, PAD may be passive (analyzing light reflections or micro-movements to confirm liveliness) or active (prompting small actions like blinking or turning your head). Either way, the system quietly decides whether the subject in front of the camera is a real person or a fake representation. When capture systems combine liveness and image quality checks, they become far harder to fool.
This dual approach, combining quality and authenticity, prevents many problems before they even start. It reduces the number of re-captures, shortens queues in high-traffic environments, and protects users from fraud. Instead of relying on passwords or PINs that can be stolen, these systems make sure the identity being presented belongs to a living, breathing human being standing in front of the sensor.
What’s the Difference Between a Biometric Sample and a Template?
A sample is the raw capture, which can refer to a face image or a fingerprint image. A template is the compact feature representation extracted from that sample and used for comparison. In many systems, only the template is stored long-term, while raw images are discarded or tightly controlled. This distinction appears in Innovatrics’ developer documentation and in many standards and products.
What Happens to the Collected Sample?
A captured sample (the image) can be discarded, stored, or stored in part depending on policy and law. Many architectures convert the sample into a template and keep only the template, treating the raw image as ephemeral. The international standard ISO/IEC 24745 describes biometric information protection, including confidentiality, integrity, and renewability/irrevocability, important if templates must be re-issued (e.g., after a compromise, you can revoke a protected template but not someone’s face). Aligning capture policies to this standard supports privacy by design and makes your documentation defensible.
When capture happens on a personal device, on-device processing and minimal data flows reduce risk. If images must leave the device, encrypt them in transit and at rest, restrict retention, and separate identifiers from samples. Clear notices and consent dialogs (explaining what is captured and why) increase user trust and help satisfy regional privacy regulations that may apply to biometric data.
