eIDV (Electronic Identity Verification) definition
Electronic Identity Verification (eIDV) is the digital process of confirming that a real, live person is who they claim to be. In practice, it blends three kinds of checks: authenticity of evidence (typically a government ID), ownership of that evidence (biometric face match between a selfie and the document portrait, with liveness to stop spoofs), and context or risk signals (e.g., sanctions, device integrity, and simple plausibility checks). When these checks agree, the system has enough confidence to approve an account opening, issue a credential, or grant access, often within seconds.
What Is eIDV and How Does It Differ from Authentication?
Electronic Identity Verification (eIDV) is a digital process for proving who someone is with the same reliability as an in-person ID check. It uses trusted signals like signed data from e-passports or eIDs, biometric face matching, and liveness detection to confirm that a real person (not a photo or video) is present. Additional checks, such as device integrity and IP consistency, add layers of protection. Together, these create a secure and efficient way to verify identity remotely, reducing fraud and simplifying onboarding.
Verification and authentication serve different purposes. eIDV is the first-time proof, confirming someone’s true identity. Authentication happens afterward and simply verifies that the returning user is the same person, usually through faster methods like passkeys or device biometrics. Think of eIDV as registering for a library card, and authentication as showing it the next time you visit.
By replacing in-person ID checks with digital ones, eIDV scales easily across countries and industries. When implemented according to international standards, it makes remote onboarding fast, secure, and reliable, which builds a foundation of trust for all future logins and digital interactions.


Why Organizations Use Electronic Identity Verification?
The big three drivers are regulation, risk, and reach. Banks, fintechs, telecoms, marketplaces, and public services must “know their customer” and prove they checked properly. eIDV provides an auditable way to meet those obligations while reducing manual reviews and cutting the time between a user’s first tap and “you’re approved.” It’s also essential for cross-border services: a digital process can verify someone in another city or another continent without shipping paper or scheduling video calls for everyone.
User experience is the other half of the story. People expect to complete important tasks on their phones, in minutes, without a store visit. With a good capture flow, such as clear prompts for lighting and pose, automatic glare detection on the ID, and instant re-tries on blurry selfies, most applicants sail through on the first try. The result is higher conversion and less abandonment, which matters just as much to a public service trying to reach citizens as it does to a bank competing for new customers.
What Are the Core Components of an eIDV Flow?
Document Verification
Document checks start with images of the front and back (or the data page for passports). The system validates visible security features and the machine-readable zones, looks for tampering, and cross-checks fields for internal consistency. If the document has an NFC chip, as with modern passports and many national IDs, the app can read it and verify the digital signatures against trusted roots. That cryptographic validation is a step change in assurance because it confirms the data exactly as the issuer wrote it.
Even without NFC, careful optical analysis is powerful when combined with other signals. The goal is not just to say “this looks like a real ID,” but to produce a verdict that’s explainable later: which checks were run, what evidence supported the outcome, and where the confidence limits lie. That explanation builds regulator trust and makes troubleshooting easier if a customer appeals.
Biometric Face Verification & Liveness
Next comes the selfie. A modern flow guides the user to frame their face, checks sharpness and exposure in real time, and only captures when quality is high enough. The system then compares the selfie to the document portrait, using a face-matching model tuned for low false acceptances. Liveness (also called Presentation Attack Detection) runs alongside to spot attempts to fool the camera – printed photos, screens, masks, or injected video.
Why combine match and liveness? Because together they answer two questions: Is the right face here? And is it a real, present human? That closes off the most common and scalable attack paths, while still feeling natural to the user. No puzzles, no awkward head gymnastics, just a steady look at the camera for a second or two.
Data Checks and Risk Signals
Identity is also about context. Services screen applicants against sanctions and PEP lists, and in regulated settings where it’s allowed, corroborate addresses or attributes against authoritative sources. Device and network checks add guardrails: a rooted phone, a headless emulator, or an IP hopping between distant geographies might push a case to manual review. None of these by itself should make or break a decision; the power lies in orchestration that weighs them sensibly.
Decisioning and Audit Trail
Finally, all signals converge into a decision: pass, fail, or review. A good platform explains itself in the form of thresholds, model versions, or risk rules so an auditor can reconstruct what happened later. That doesn’t just satisfy compliance as it speeds customer support too. If someone fails, reviewers can see exactly why and either confirm the outcome or correct it.
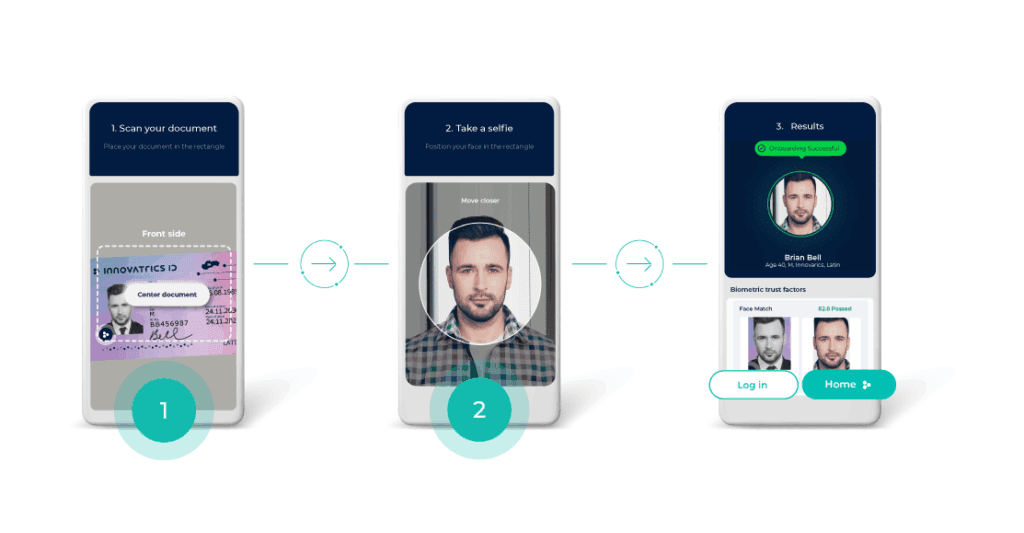

How eIDV Works in Practice?
A typical flow starts when the user claims an identity and scans their document. The app immediately nudges for better lighting or angle, reads the MRZ or barcode, and if supported, invites the user to tap the document for NFC chip reading. Chip validation checks signatures against trusted roots, which makes it very hard to pass off a forged document as real.
Then the selfie comes after. The camera captures only when quality is high enough, liveness runs to block spoofs, and the face match links a live person to a document portrait. Surrounding checks like sanctions, device integrity, IP/geolocation plausibility fill in the risk picture. A decision engine weighs it all and either approves, rejects with reasons, or sends the case to a reviewer with a crisp evidence summary. The full trail – what was checked, by which engine, with what thresholds stays available for audits.
How to Make eIDV More Accurate and Reduce Friction?
Chip-first policies are an easy win. If a document has an NFC chip, read it. That single step converts a fuzzy optical image into cryptographically verified identity data and usually improves acceptance rates because there’s less guesswork. Pair it with a well-tuned selfie + liveness step, and most scalable attacks (stolen photos, printed cards, replay videos) never make it to manual review.
Channel integrity matters as much as the checks themselves. Guard the capture pipeline against video injection and emulator tricks. If the camera feed isn’t trustworthy, even the best liveness won’t save you. Finally, orchestrate by risk: tighten checks for high-value limits or cross-border flows, ease them (within policy) where risk is low, and always keep the user experience clear and inclusive.
Case in Practice: Signicat’s EU-Scale Remote Proofing
Signicat operates across a patchwork of European rules and had to deliver remote identity proofing with legal validity equal to an in-person visit. Their upgraded VideoID approach layered a strong face-verification engine with passive liveness and injection defenses, then aligned these technical controls to the regulatory frameworks – eIDAS/ETSI for trust services and SEPBLAC for Spain’s video identity. The result was fewer false rejections, better outcomes for harder-to-capture users, and a smoother path to issuing qualified credentials.
The broader lesson is that standards-aligned biometrics don’t just prevent fraud but also enable equivalence by giving regulators confidence that a remote flow can stand in for the old “show up with your passport” model. That’s how eIDV moves from a clever app to a critical infrastructure for digital economies.
eIDV vs. eID: What’s the Difference?
eIDV is the process while eID is the product. You verify once with strong evidence, then receive a reusable credential, such as a national eID, bank-ID, or soon, an EUDI Wallet credential that you can present later. In that world, first-time onboarding is still an eIDV problem. Everyday logins become a simple, privacy-preserving exchange of verified attributes from your wallet.
As wallets roll out, services will do fewer repeat captures. Instead, they’ll accept digitally signed attributes like “is this person over 18?”; “is this the holder of account X?”, without re-scanning documents. eIDV remains essential for issuing those credentials and for recovery when a user changes devices or loses access.
Where Is eIDV Used?
In banking and fintech, eIDV is now table stakes for account opening, card issuance, and crypto exchange onboarding. Telecoms use it for SIM registration and number portability, reducing fraud tied to account takeovers. Public sector programs use it to issue digital credentials for tax portals, health records, and benefits. In trust services, it underpins the remote issuance of qualified certificates. Marketplaces and gig platforms apply it for merchant vetting, driver identity, and age-gated goods.
Across all these, the thread is the same: make it easy for good users to prove who they are, and make it hard for impostors to slip through without sending everyone to a counter.