Video Injection Prevention definition
Video injection prevention is a set of technical controls, architectural patterns, and operational practices that detect, block, and mitigate attempts to feed falsified or tampered video streams into biometric, surveillance, and remote-verification systems. These attacks enable fraudsters to bypass identity checks, impersonate users, or manipulate automated decision-making by substituting genuine camera feeds with prerecorded, synthetic, or modified video content.
Why Does It Matter?
In the era of digital identity verification and remote onboarding, biometric security is paramount. However, the rise of sophisticated digital fraud, especially those leveraging hyper-realistic deepfakes has rendered traditional security measures, including basic liveness detection, insufficient.
Biometric authentication relies on the assumption that the camera captures a live, genuine, real-time user. If attackers can replace this feed with a fabricated video, even the most advanced facial recognition system may be fooled. Video injection prevention may stop this by ensuring camera integrity, monitoring data flow, and validating the authenticity of captured frames.
The core challenge today is Video Injection Attack – a digital threat that bypasses the physical camera entirely to feed fraudulent video data directly into an identity verification system.


Understanding Video Injection Attack
Video injection attacks represent a more advanced and dangerous threat to biometric authentication compared to traditional presentation attacks. It involves fraudsters disabling or hijacking web or mobile cameras and replacing live feeds with prepared video streams to bypass biometric authentication.
Unlike traditional presentation attacks where a fraudster physically shows a photo or mask to a camera, video injection attacks operate at the software or hardware level, making them significantly more dangerous and harder to detect.
Types of Video Injection Attacks
Replay Attacks
Attackers inject pre-recorded videos of real verification sessions and stream them as if they are live. If a verification system doesn’t check the timing or prevent the reuse of old recordings, these attacks can easily succeed.
Deepfake Injection
Fraudsters use AI to generate realistic fake videos of a person’s face, creating synthetic identities or impersonating real individuals. Recent incidents demonstrate the severity of this threat, where Vietnamese police uncovered a gang that allegedly laundered around $38 million by generating fake facial scans using AI-powered biometric fraud.


Virtual Camera Exploitation
Attackers use software that creates a virtual webcam device, feeding pre-recorded or synthetic video instead of a real camera feed. The operating system treats this virtual camera as legitimate hardware, allowing fraudulent content to pass through undetected.
Hardware-Based Injection
Sophisticated attackers leverage physical devices like USB video capture cards or HDMI screen grabbers to fool systems. These devices play fraudulent videos but appear to the network as legitimate camera sources.
API and Code Manipulation
Attackers try to trick a biometric system by replacing a live video or image from a camera with a pre-recorded video or a fake picture right when the application is running.
Essential Components of Video Injection Prevention
Active Liveness Detection
Active liveness detection requires users to perform random actions during verification, such as blinking, smiling, or turning their head. The randomized nature of these challenges makes it extremely difficult for attackers to use pre-recorded or AI-generated videos successfully. This forms the first line of defense in establishing that a live person is present during authentication.
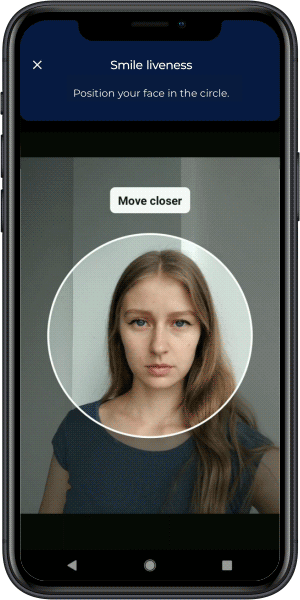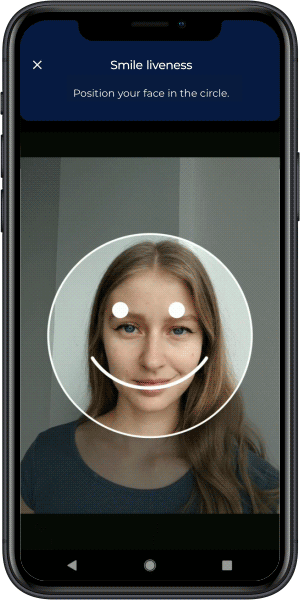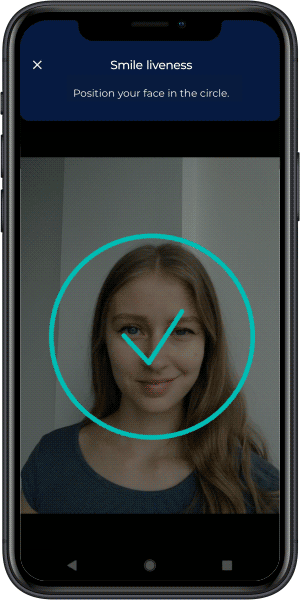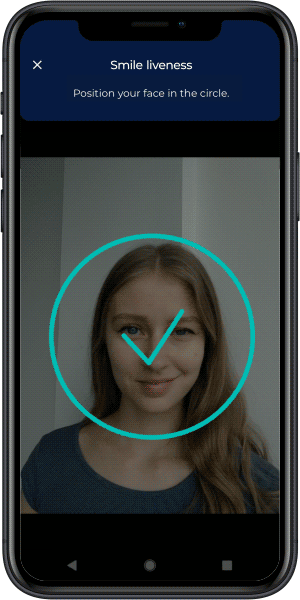

Video Source Verification
Ensuring data integrity from a user’s camera to a company’s server through video source control is essential. This includes encrypted communication channels, virtual camera detection capabilities, and sophisticated monitoring for timing inconsistencies or other anomalies that indicate manipulation.
Deepfake Detection Technology
Advanced biometric systems incorporate machine learning models trained on extensive datasets of authentic and manipulated content. These models identify anomalies such as unnatural blending at facial edges, inconsistent lighting or shadows, or distorted eye reflections that reveal deepfake manipulation.
Platform Security Considerations
System vulnerability to injection attacks often depends on the operating system, with iOS environments generally offering stronger default security through Apple’s integrated hardware-software control. Conversely, Android’s more open ecosystem offers greater flexibility but requires developers to implement additional security layers to prevent such attacks.
Multi-Layered Defense Architecture
Effective video injection prevention demands a comprehensive security strategy combining multiple defense mechanisms. Single-point solutions are insufficient against determined attackers who often combine techniques, such as injecting authentic video while overlaying deepfake faces to circumvent individual security measures.
Why It Matters for Governments and Businesses
- Risk to identity platforms: Video injection undermines the integrity of remote identity verification and biometric onboarding, enabling synthetic identity fraud and false acceptances. This threatens public services, border control, financial KYC, and e‑government programs.
- Operational and reputational harm: A single successful injection event can cause financial loss, legal exposure, and erosion of citizen or customer trust.
- Regulatory scrutiny: Agencies increasingly expect demonstrable anti‑tampering and anti‑spoofing measures as part of compliance and procurement requirements.
Detection and Prevention Techniques
Cryptographic Device Verification
Establish chains of trust using cryptographic signatures, thereby verifying that video feeds originate from authenticated devices and have not been tampered with during transmission.
Liveness and Consistency Analysis
Combine active and passive liveness checks that analyze temporal micro‑movements, physiological signals, and cross‑modal consistency (audio + video) to detect replayed or synthetic media.
Multi-Factor Authentication Integration
Combine biometric verification with additional authentication factors, consequently ensuring that even if one element is compromised, unauthorized access remains prevented.
Runtime Environment Hardening
Protect the host and camera stacks, restrict camera access, use secure SDKs, enforce OS integrity checks, and monitor for API hooking or suspicious processes.
Regular Security Updates
Stay ahead of evolving attack methodologies by continuously updating detection algorithms based on emerging threat intelligence and newly discovered attack vectors.
The Future of Video Injection Prevention
As AI capabilities advance, both attack sophistication and defensive technologies continue to evolve. Organizations must adopt proactive security postures, investing in cutting-edge detection capabilities and maintaining vigilance against emerging threats. As digital identity verification becomes standard across government and enterprise environments, protecting the integrity of video streams is no longer optional but mandatory.
The development of industry-specific standards and certification frameworks for video injection prevention represents a critical next step. Enhanced standards will provide organizations with clear benchmarks for security effectiveness and help establish baseline protection requirements across sectors.