Image Capture
A high-resolution image of the iris is captured using specialized cameras or scanners designed for iris recognition.
Innovatrics iris recognition is exceptionally accurate and ideal for high-security applications where maximum reliability is required.
Talk to our team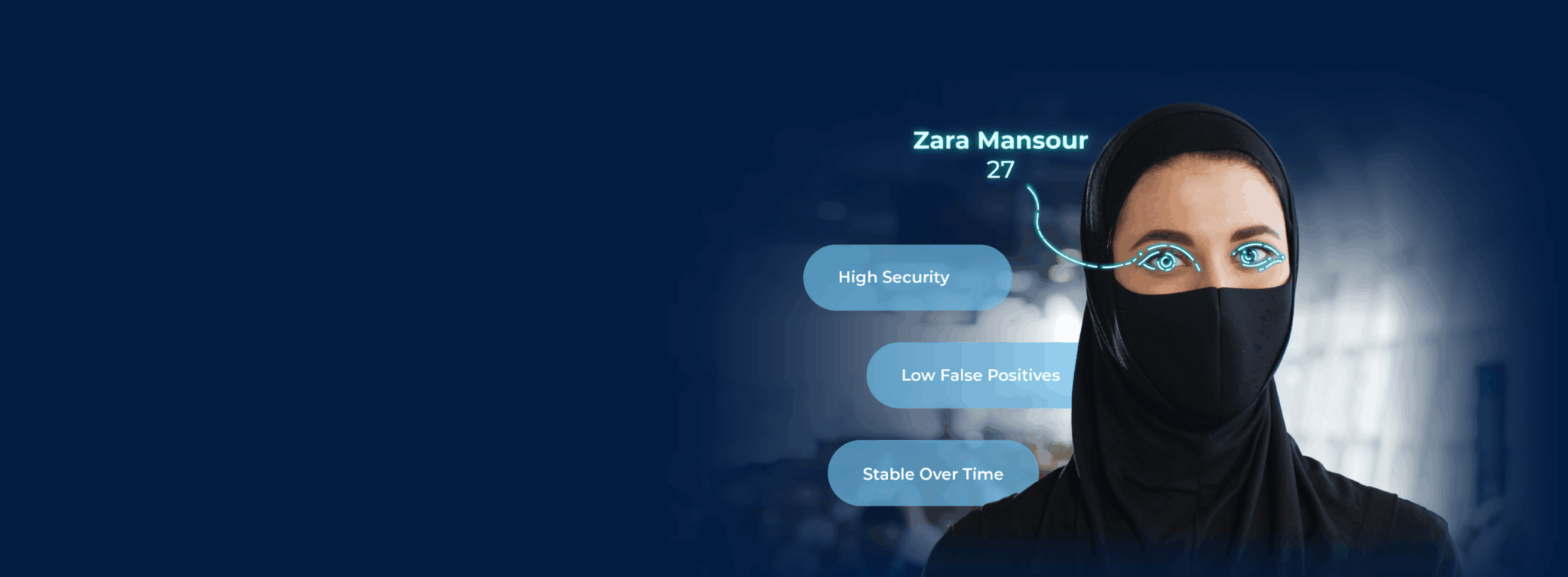

Iris recognition technology is based on the analysis of unique patterns found in the colored ring surrounding the pupil of the eye. These intricate structures form during early childhood, remain stable throughout life, and are distinct enough to serve as highly reliable identifiers. By scanning and comparing these patterns, iris recognition systems can verify or establish identity with exceptional accuracy, making it one of the most secure biometric modalities available.
Today, it is widely applied across multiple sectors. Governments deploy it for national ID programs, border control, and voter registration, ensuring individuals can be uniquely and reliably identified. Airports and transportation hubs use it to expedite passenger processing, while financial institutions and enterprises employ it for secure authentication. On the consumer side, iris recognition is integrated into mobile devices and access systems, offering fast, contactless, and hygienic identity verification in everyday life.


Widely used in airports, checkpoints, banking, and secure facilities where maximum reliability and fraud resistance are essential.
Iris patterns are highly distinctive and stable over a lifetime, providing one of the lowest false match rates of any biometric modality.
Iris structures do not change with age, wear, or external conditions, ensuring consistent identification throughout a person’s life.
In some situations, iris scanning may require no physical touch, making it hygienic, fast, and reliable even in challenging environments.

A high-resolution image of the iris is captured using specialized cameras or scanners designed for iris recognition.
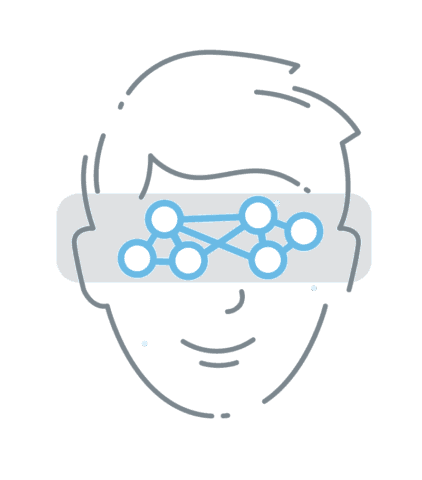
The system uses deep learning to analyse the iris, capture its unique patterns and extract distinctive features.
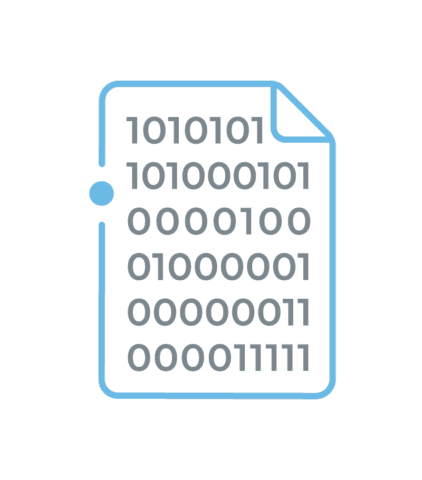
These features are converted into a digital template, representing the individual’s iris in a format that can be stored, compared and identified.
Since 2004, Innovatrics have consistently ranked among the best in the world in independent biometric benchmark evaluations and certifications.
Essential for large-scale iris recognition in one-to-many identification. Strong IREX 10 performance ensures faster, more accurate searches across massive databases.